In our weather project, we use a third-party service to fetch weather data, such as the real-time temperature in a city. The third party provides an API token that helps identify our user account and manage permissions, QPS limits, and billing usage. However, hardcoding the token and deploying it to AWS is not a good practice, as it could lead to credentials leak if the server is hacked. Moreover, if we deploy multiple servers, updating the token across all of them becomes difficult if it changes in the future.
To address this issue, I have explored a solution for managing API credentials securely on AWS.
AWS Systems Manager Parameter Store
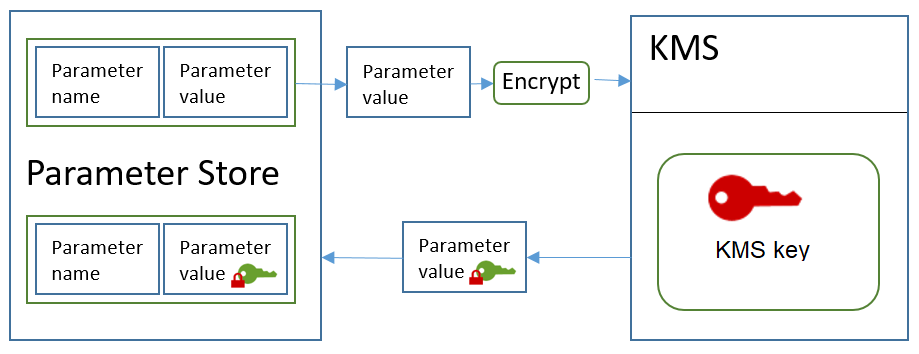
AWS Systems Manager Parameter Store offers a robust solution for securely storing configuration data and secrets, including API keys, passwords, and license codes. With centralized management and fine-grained access control, it serves as an effective tool for handling sensitive credentials.
Key benefits:
- Encryption at rest: Parameters can be encrypted using AWS Key Management Service (KMS).
- Version control: Parameter values can be versioned, allowing rollback if needed.
- Access control: You can restrict access with IAM policies to limit who or what can read the secrets.
- Integration: It integrates seamlessly with other AWS services such as Lambda, EC2, and ECS, enabling easy retrieval of credentials during runtime without hardcoding them.
Implementation
In our weather project, the API token is securely stored in AWS Systems Manager Parameter Store, while the Django REST Framework application runs on an EC2 instance. Here’s how we set up and retrieve the token securely:
Create the Parameter
Store the API token as a SecureString parameter using the AWS Console:Attach an IAM role to the EC2 instance that grants permissions to access the Parameter Store parameter.
Fetch the API Token in Django
Use AWS SDK for Python (boto3) to retrieve the token securely at runtime:import boto3 from botocore.exceptions import ClientError import logging logger = logging.getLogger(__name__) def get_api_token(): ssm = boto3.client('ssm', region_name='ap-southeast-2') try: response = ssm.get_parameter( Name='/weatherproject/apiToken', WithDecryption=True ) return response['Parameter']['Value'] except ClientError as e: error_code = e.response['Error']['Code'] error_msg = f"Failed to retrieve API token: {error_code} - {str(e)}" logger.error(error_msg) raise ValueError(error_msg)Use the token in Django REST Framework views and remove the hardcoding.
Keeping the API token entirely separate from the source code and environment variables significantly improves application security. It also simplifies credential management—any updates made in AWS Parameter Store take effect automatically, without requiring code changes or redeployment. This allows for a greater focus on building features, rather than managing the risk of sensitive information leaks.
Some findings and thoughts
- Parameter Store offers a secure and cost-effective way to manage secrets, though AWS Secrets Manager provides more advanced features at a higher cost.
- Updating the API token in Parameter Store instantly applies to all services without redeployment, simplifying credential management.